Practice ntds.dit File Part 3: Password Cracking With hashcat – Wordlist
Now we will use hashcat and the rockyou wordlist to crack the passwords for the hashes we extracted in part 2.
Fast online lm hash cracking. Use browser with frames support. Now we will use hashcat and the rockyou wordlist to crack the passwords for the hashes we extracted in part 2. With this command we let hashcat work on the LM hashes we extracted: hashcat-3.00 hashcat64.exe -a 0 -m 3000 -potfile-path hashcat-rockyou-lm.pot -username lm.ocl.out rockyou.txt Option -a 0 instructs hashcat to perform a straight attack.
With this command we let hashcat work on the LM hashes we extracted:
Option -a 0 instructs hashcat to perform a straight attack.
Option -m 3000 informs hashcat that we provide LM hashes.
Option –username informs hashcat that the hash file lm.ocl.out includes usernames.
Argument lm.ocl.out is the hash file.
Argument rockyou.txt is the wordlist.
I also use option –potfile-path to instruct hashcat to use a specific pot file (a file containing the cracked hashes with corresponding passwords).
Here is the output:
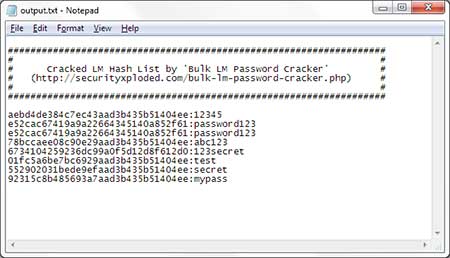
To display the cracked passwords, we use option –show:
Option –show instructs hashcat to display the cracked passwords.

Option -m 3000 informs hashcat that we provide LM hashes. This is necessary for –show.
Option –username informs hashcat that the hash file lm.ocl.out includes usernames.
Option –outfile-format 2 instructs hashcat to output the password without the hash.
Argument lm.ocl.out is the hash file.
I also use option –potfile-path to instruct hashcat to use a specific pot file (a file containing the cracked hashes with corresponding passwords).
Here is the output:
As you can see we cracked most of the passwords for users 1 through 20, except when the password is longer than 14 characters. Also remark that all passwords are uppercase.
With this command we let hashcat work on the NTLM hashes we extracted:
The options and arguments are almost the same as for the LM command, except:
Option -m 1000 informs hashcat that we provide NTLM hashes.
Argument nt.ocl.out is the hash file.
Here is the output:
Remark that this time we cracked all passwords for users 1 through 20 (also the ones longer than 14 characters), and with the proper case.
Background – The SAM
The Windows registry contains a lot of valuable information for cyber investigators and security analysts alike. The registry lives mainly in C:System32config for the local machine, with user specific registry items contained in each user's profile in a hidden file named NTUSER.DAT. The SAM file is part of the local machine hive and it is where you'll be able to find information regarding user accounts. This is also where account credentials are stored.
What is an NTLM hash?
New Technology LAN Manager, or NTLM is a protocol suite in Windows that maintains authentication. The NTLM hash is unsalted, meaning that it is not modified with a known value. This enables the NTLM hash to be used in a practice called 'Pass the Hash' where the hash value is used for authentication directly. The NTLM hash appears in the following format:
The information can be broken down into three sections. The first shows a username followed by a colon and double quotes. The colon and quotes can be safely ignored as they are not needed to crack the password. A user's relative identifier would appear in this spot (500 for Administrator, 501 for Guest, 1000 for first user created account). The next string of characters is the LM hash and is only include for backwards compatibility. The last section is the most important for cracking, this is the NT hash. The NT hash is commonly referred to as the NTLM hash, which can be confusing at the start.
Crack Ntlm Hash
How do you get the NTLM hash?
Option -m 3000 informs hashcat that we provide LM hashes. This is necessary for –show.
Option –username informs hashcat that the hash file lm.ocl.out includes usernames.
Option –outfile-format 2 instructs hashcat to output the password without the hash.
Argument lm.ocl.out is the hash file.
I also use option –potfile-path to instruct hashcat to use a specific pot file (a file containing the cracked hashes with corresponding passwords).
Here is the output:
As you can see we cracked most of the passwords for users 1 through 20, except when the password is longer than 14 characters. Also remark that all passwords are uppercase.
With this command we let hashcat work on the NTLM hashes we extracted:
The options and arguments are almost the same as for the LM command, except:
Option -m 1000 informs hashcat that we provide NTLM hashes.
Argument nt.ocl.out is the hash file.
Here is the output:
Remark that this time we cracked all passwords for users 1 through 20 (also the ones longer than 14 characters), and with the proper case.
Background – The SAM
The Windows registry contains a lot of valuable information for cyber investigators and security analysts alike. The registry lives mainly in C:System32config for the local machine, with user specific registry items contained in each user's profile in a hidden file named NTUSER.DAT. The SAM file is part of the local machine hive and it is where you'll be able to find information regarding user accounts. This is also where account credentials are stored.
What is an NTLM hash?
New Technology LAN Manager, or NTLM is a protocol suite in Windows that maintains authentication. The NTLM hash is unsalted, meaning that it is not modified with a known value. This enables the NTLM hash to be used in a practice called 'Pass the Hash' where the hash value is used for authentication directly. The NTLM hash appears in the following format:
The information can be broken down into three sections. The first shows a username followed by a colon and double quotes. The colon and quotes can be safely ignored as they are not needed to crack the password. A user's relative identifier would appear in this spot (500 for Administrator, 501 for Guest, 1000 for first user created account). The next string of characters is the LM hash and is only include for backwards compatibility. The last section is the most important for cracking, this is the NT hash. The NT hash is commonly referred to as the NTLM hash, which can be confusing at the start.
Crack Ntlm Hash
How do you get the NTLM hash?
The answer to this depends on the target system state. Mimikatz is likely the most popular tool for the job. If it is powered down, then the targets hard drive can be removed and mounted (ideally with a write blocker) and the registry files can be accessed. In this scenario, Mimikatz will be used against the SAM file and the SYSTEM file. An example of the command can be seen below.
Defeating the Hash
Once the NTLM hash has been obtained, there are several methods of determining the plain text password. Bear in mind that cryptographic hashes are one-way-functions that cannot be decoded. In order to determine the actual password, we must compare the hashes of known strings to determine if it is a match to the sample.
Cracking
Depending on the hardware of a computer, this method could take anywhere from hours to weeks. I will cover the process I took to begin cracking the hashes. There are various tools available, but I will be focusing a tool named Hashcat due to familiarity. Hashcat, is an opensource password hashing suite that can leverage the power of graphics cards to aid in the calculations. Hashcat itself supports cracking via a dictionary, bruteforce, or a combination there-of. A straight dictionary attack would be the fastest method, but it would require that the password be in the dictionary verbatim. A collection of wordlists can be found on GitHub with the correct search term. A bruteforce method would be slow, but as long as the mask matches it is a more inclusive search method.
In the above screenshot, I chose to use a GUI frontend on Hashcat for demonstration purposes. I'll be starting a bruteforce attack assuming the password is between 1 and 9 characters in length and has uppercase, lowercase, and/or numbers in it. This can be seen by the character set #1 with ?l?d?u. The question mark here is used as a wildcard.
Hashcat will then try all the possible solutions to match the sample hash. In my case it is working at 7466MH/s (or 7,466,000,000 hashes a second). Even with the speed, this will take time.
There must be a better way
I am a firm believer that success in this field has a big part to do with being able to recognize when someone has already done the hard work for you. Most of the time you can find the answers you are looking for by asking the right question to the all-knowing Google. A quick search for NTLM hash cracker will return with a website called hashkiller.co.uk, which just happens to be who created the GUI for Hashcat.
Here, we can take the NT hash from the provided list and see if they have been seen before. I'll be using the following as an example. The NT hash is highlighted.
Perfect, the password to the user account 'cmonster' is 'cookie'. This method works for most of the hashes found on the list. There are a few that are not found. I have listed them below.
You may have noticed that the hash for 'Guest' and 'victim' are identical, they must have the same password. We find one, we find both. My thought process for this part of the challenge was to return to Google and ask a different question. Autodesk building design suite for mac osx. Knowing that a hash is a unique string, I figured it might be worth while to paste the hash directly into the search box and see what it returns. Perhaps it's referenced elsewhere.
I stumbled upon the answer in the very first result. It became very obvious to me.
The account I was attempting to find the password for was Guest. The Guest account (sid 501) in Windows does not have a password by default, so it would make sense that it is blank. This must also be true for the victim account.
Unfortunately, I was unable to find any matches to two of the hashes using the easy method. My computer will be set to manual crack these two hashes over the next 8 weeks.
Nt Hash Converter Online
Below are the hashes that were able to be defeated using simple research and online tools.

